The Health Insurance Portability and Accountability Act of 1996 (HIPAA) has been around for over twenty years. Those involved in medical research and deals directly with patients are well aware of the requirements of HIPAA compliance. However, the range of compliance understanding from market researchers varies from person to person, mostly as a result of modern market research complexity using web-enabled tools. Not everyone is aware of what specifically to do to ensure compliance is met. That leaves the question: how exactly can a researcher determine if their third-party market research facilitators meet and maintain compliance with the HIPAA Privacy and Security Rules?
In this eGuide, we’ve compiled the guidelines necessary to help you the researcher, stay HIPAA compliant in web-enabled market research.
Keep reading to learn:
| How a researcher can determine if compliance standards are being met by third-party partners |
| What researchers can do to help protect themselves when engaging with third-party partners |
| What steps a market researcher facilitator can take to support the compliance needs of its clients |
What Does it Mean to be HIPAA Compliant?
Being HIPAA compliant is all about putting principles into practice such as having training and policies within your organization so employees are aware of how to protect health information in their everyday work.
For those working in market research who are looking for vendors and service providers of facilitate web-enabled market research, you are looking to avoid risks to make sure that you are HIPAA compliant when conducting your research.
HIPAA is mostly about how data is handled every day.
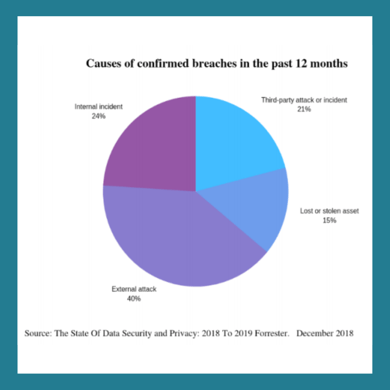
Unfortunately, third parties, vendors, or market research service providers are not exempt and can often be exposed to security breaches. This doesn’t only risk exposing your data, but can also negatively impact your business where you could face investigations and penalties.
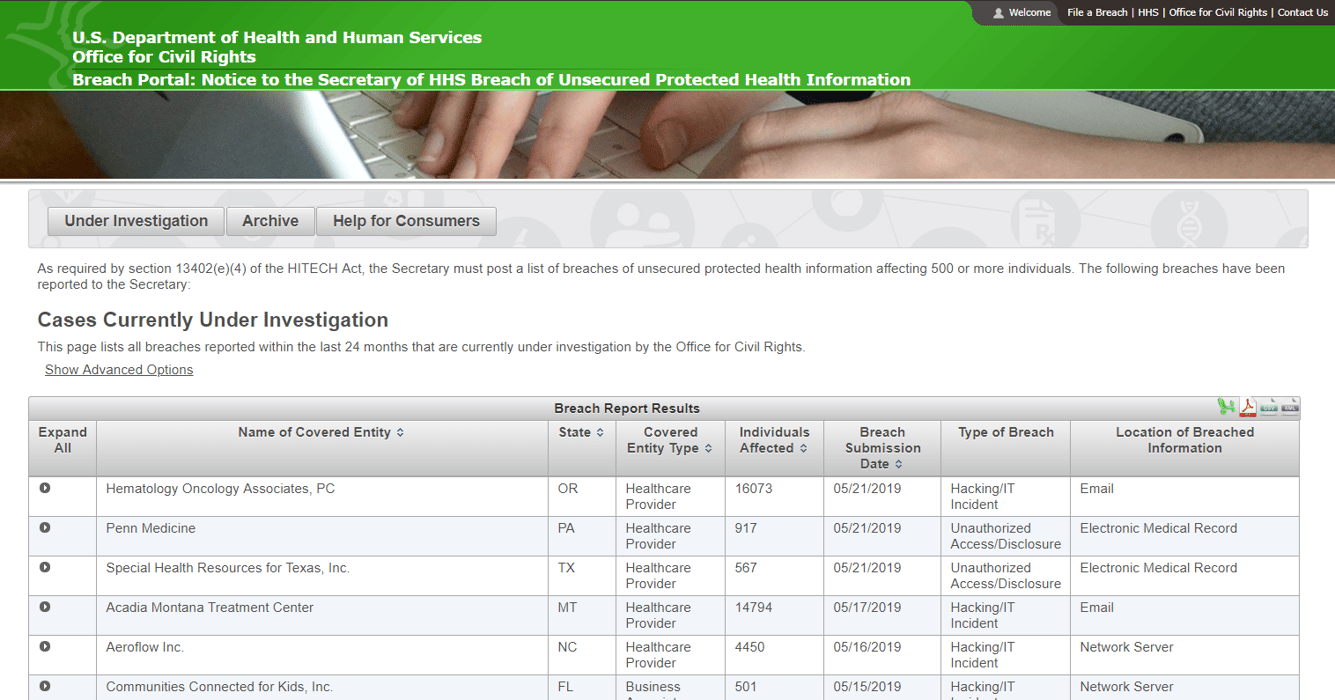
A good example of this is the "HIPAA Wall of Shame," formally called a Breach Portal by the U.S. Department of Health and Human Services website. This contains all the details of covered entities or business associates that have been investigated for data breach along with the type of breach and the individuals that were affected. Getting on this wall of shame has a high risk of reputation damage since your name will never come off as it’s a permanent and public database.
Look for Healthcare Experience
One of the ten ways to stay HIPAA compliant in web-enabled research, particularly when you’re looking for vendors and service providers, is to look for healthcare experience.
When you’re engaging with these market research service providers, you would want to ask some key questions:
| Is the supplier aware of and ready to meet requirements protecting health info?When is the last time they performed a privacy risk assessment?Have they been forthcoming in sharing how they handle data?Do you see evidence of how the data is protected when sharing data with them? |
Gauge if their business processes are well documented. Make sure they have assessed how each process can impact the privacy of individuals and their health information. Transparency here is very important as well. You need to know how any data that you are transmitting is going to be handled, where it goes, and who has access to it.
To ensure data is protected, make sure that service providers are facilitating measures to transfer data securely and with encryption as required by HIPAA. The same goes for erasing data securely either with a retention policy or evidence of the technical standards to which they disposed of the electronic data.
Engage in Business Associate Agreements
Suppliers should also be ready and willing to sign a BAA as it is a violation not to have one in place. Additionally, even cloud providers such as Amazon, DropBox, Google, etc., who only transmit PHI without actual access are considered Business Associates, even if the data is encrypted.

Who are these Business Associates?
Business Associates are service providers to the entities that have protected health information (PHI) - researchers, law firms, transcriptionists, facilitators, and hosted software providers. In the case of a data breach, they are liable for both notification and minimizing harm to individuals by unauthorized access to their data.
Look for Consent Management Practices
Managing consent to the storage or handling of PHI is important. But how exactly can this be done? First and foremost, you need to know if your provider has the basics covered to meet GDPR and HIPAA requirements for consent.
To check a market research service provider's consent management processes, you need to do the following:
- Look at their website
Acceptable market research standards require notices & consent forms to be up to date. Check that their privacy policy has been recently reviewed.
- In line with HIPAA requirements, find out if suppliers have designated Privacy and Security Officers
These officers are the company’s point of contact for relevant privacy and security rules. They will take responsibility for the respective privacy and security requirements such as the enforcement of training and the implementation of internal policies or protocols for security (technical and non-technical safeguards).
- See if they have a policy or process to deal with individual requests for accounting of disclosures
HIPAA gives rights to individuals to have access to their PHI, also known as an accounting of disclosure to their PHI. They have the right to be able to request organizations to tell them where their data has been sent.
Data minimization is a core principle of privacy protection, it reduces the risk of non-compliance or breach. Simply put, if you don’t have it, it can’t be stolen or misused.
Here are some ways to minimize your use of data:
| Reduce risk by using the absolute minimum data necessary for your research.Anonymize respondent data as much as possible. (Pseudonymization is not enough!)Partners should be able to tell you the minimum information required to provide their services. Consider options for audio and face masking. (Voice prints, recordings, and full-face images are considered PHI.) |

It is important to note that there is not really such a thing as HIPAA-compliant technology.
It's about how the users implement the privacy safeguards when using the technology.
Track Your Data
 Most providers offer services globally - and even those that don't - are still most likely subject to GDPR as well as HIPAA. In lieu of this, vendors should have thorough data maps of their systems, data, and processes.
Most providers offer services globally - and even those that don't - are still most likely subject to GDPR as well as HIPAA. In lieu of this, vendors should have thorough data maps of their systems, data, and processes.
What is a data map and why is it important?
A data map shows how personal data are used and stored in the business. It is a visual representation or step by step layout identification of processes making it easier to assess business processes at every step. The data map needs to include the people who have access to it, the systems and platforms used, individual workstations, and transfers to third parties and other networks.
Look for transparency: the necessary security controls need to be clear at every stage of a process.
Expect consumers to exercise their right to privacy – suppliers should be prepared to respond to requests for an accounting of disclosure within the HIPAA required period of 45 days. Data maps make it easier to answer these requests.
Secure Your Data
Encryption of PHI is required at rest and in transit. Suppliers should be able to accommodate the use of secure file-sharing platforms such as your proprietary web app and third-party or secure file transfer protocols (SFTP). PHI should never be transferred over email. Remember, since email is generally not encrypted, it isn’t secure.
Making sure that remote access to networks is made only through the use of VPN is another way to ensure your data is secured. Even if your network does not allow for remote access, there should be regular review of firewall rules.
Confirm that there is a designated Security Officer. Make sure that someone would be accountable to respond to concerns and queries surrounding network and hardware encryption.
The risks of not securing data or not adhering to privacy policies or training are apparent and they do result in breaches of health information.
This is clearly shown in the number of U.S. residents affected by health data breaches from 2009 to 2019:
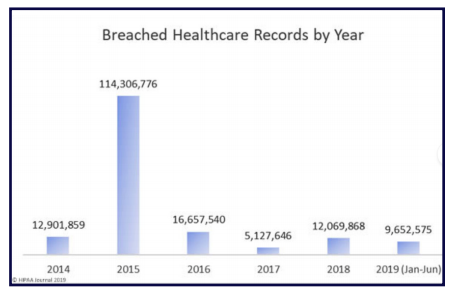
Source:
https://www.hipaajournal.com/june-2019-healthcare-data-breach-report/
Ask About Physical Security
Policies must be in place to ensure physical security. These can include:
| Security guarded buildingsBiometric authentication for entry to production areasVerified unique access for individuals to client confidential information and privacy protected informationPaperless policies where possible |
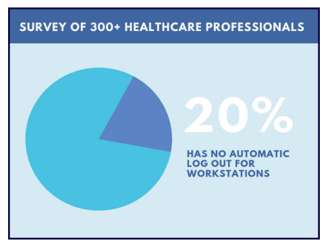
You must also make sure that the integrity or correctness of PHI is protected. There must be an automatic timeout/log out for workstations to ensure that the PHI won’t be altered or tampered with. Unfortunately, in a survey of 300+ healthcare professionals, primarily from organizations with less than 500 employees, 20% mentioned they don’t have an automatic timeout/log out for workstations.
Adopt a Security Culture

It is a HIPAA violation not to provide training for staff who handle PHI. Many companies invest in technical security but true security culture will invest in their people for they are the front line to stop unauthorized disclosures.
Training should cover the required topics as set out in the privacy rule. To make it easier for the staff to access it, set these topics out in a policy manual.
It’s also important to provide training to employees at every level with an explanation of the laws and regulations in a way that applies to what they do every day. Know the frequency of training and how new employee training is accounted for.
Maintain Awareness of Vulnerabilities
Companies must consider both regular risk assessments as required by HIPAA and risk assessments related to new or changing processes/ projects. Make sure you are able to see a list of controls that match identified gaps. Risk assessments are identifiable through data maps. You need to identify where the risks are and then address them.
Vendors must also be willing to submit to either an internal or external audit to confirm the following questions:
- Are they following their security policies?
- Do they have efficient security and privacy controls to mitigate risks? (eg. are there biometric doors? are they working?)
- Is there regular maintenance on these security
- and privacy controls?
Foster Collaboration

Before the project starts, determine how the data will be transmitted, shared, and stored.
Since you may work with vendors with multiple service offerings, analyze each tool or service from a HIPAA compliance standpoint.
HIPAA compliance is not something to be hidden or avoided.
Simply have the right policies and controls in place and you should be fine.
Conclusion
Maintaining HIPAA compliance in web-enabled market research isn’t as complicated as you think. You just have to understand how your suppliers are handling your data and whether they are willing to maintain compliance. For further assurance, demonstrate privacy and data protection awareness from the beginning of the project relationship and execute a business associate agreement for every supplier.
As long as you keep these guidelines in mind when working with third parties, vendors, or service providers, it’ll put you on the right track.



